In Short
- Introducing data paths
- Types of data paths
- Mutable data path Vs Immutable data path
- How cross-chain builders can create safer applications ?
Introduction
Blockchains are distributed, decentralized databases providing robust data validations and transparency at the cost of scalability.
Unlike centralized infrastructures, blockchains in today’s world are limited by computational power and massive storage requirements.
For starters, in traditional Web2 infrastructures like AWS, a database is stored in 2-3 replicas to prevent data corruption.
In the case of blockchain, it’s stored across multiple computers.
This is not what we’re going to explore in this article, but why am I saying this ?!
Ok, let me dive in real quick. For scalability like centralized infrastructures, such blockchains need to interoperate.
For interoperability between blockchains, multiple infrastructures are being developed by companies.
Inter Blockchain Communication (IBC) protocols are numerous in existence but without applications built on top of them, they don’t gain their motive. This article is for IBC application developers, intended to develop safer cross-chain applications.
Data Path
In traditional computer science, a datapath is a collection of functional units (including Arithmetic units or Logic units) that perform data processing operations.
I took this term because it sounds synonymous. In cross-chain applications, a data path markers data flow across chains.
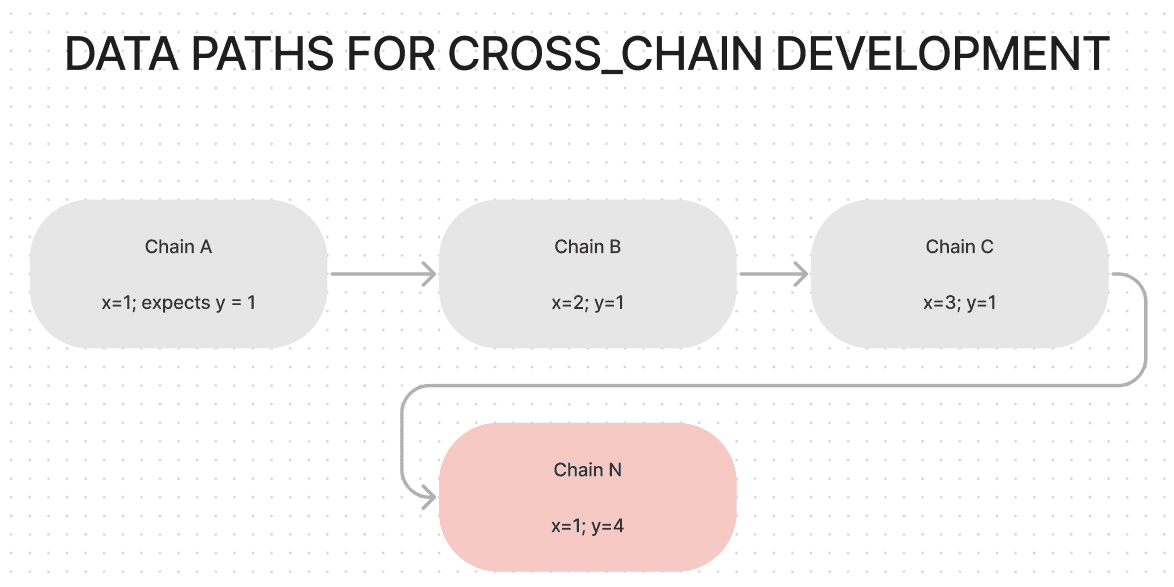
 Example of Data Path
Example of Data Path
The data paths can be cyclic or acyclic and immutable or mutable
For a cyclic data path, the start chain will be the end chain. For an acyclic data path, the start and end chains would differ.
start chain: a blockchain where the data originate end chain: a blockchain where the data executes its final state change
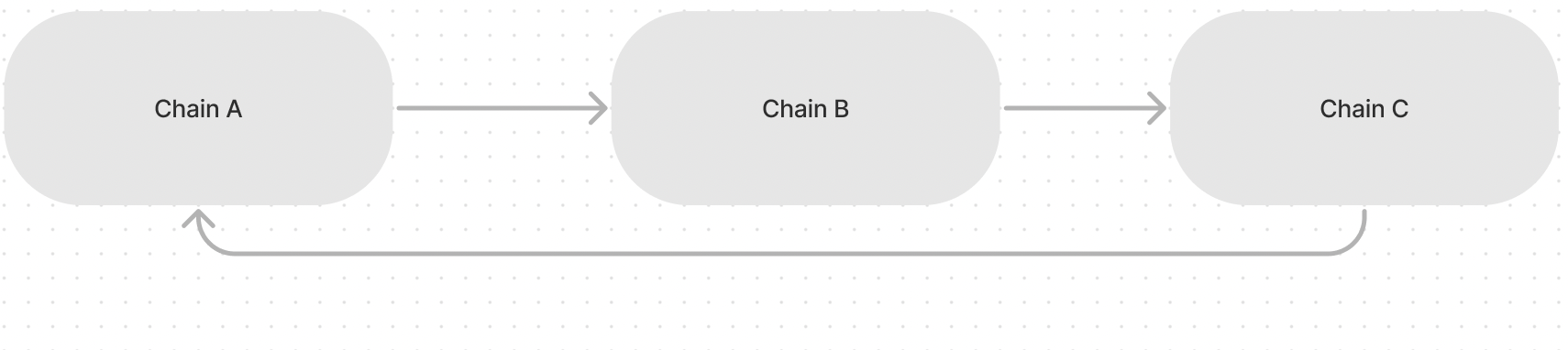 Cyclic data path
Cyclic data path
Cyclic data paths are often in cases where the start chain requires an end chain’s state changes.
Immutable & Mutable Datapath
A datapath where the state travels without any change in its entire lifecycle, such datapath is the most secure and ideal way for cross-chain applications and is known as an immutable datapath.
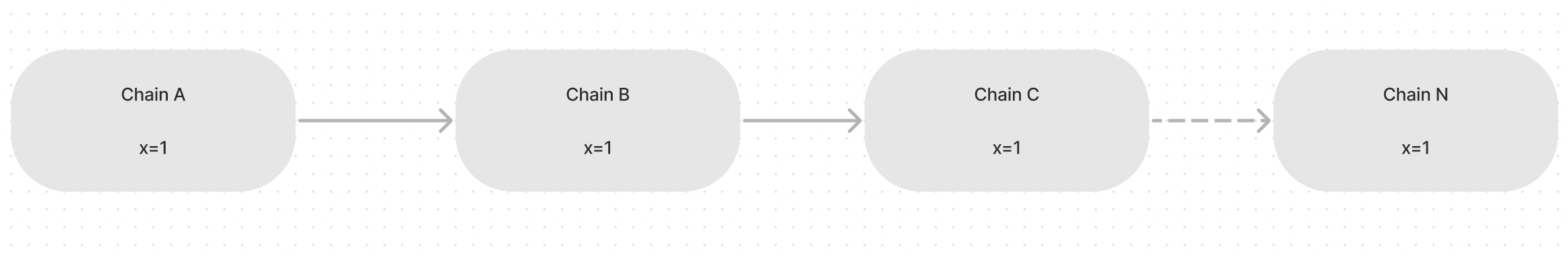 An immutable datapath where the value of x remains unchanged in its entire lifecycle
An immutable datapath where the value of x remains unchanged in its entire lifecycle
On the other hand, for a mutable datapath, the state gets updated in its lifecycle by intermediary blockchains.
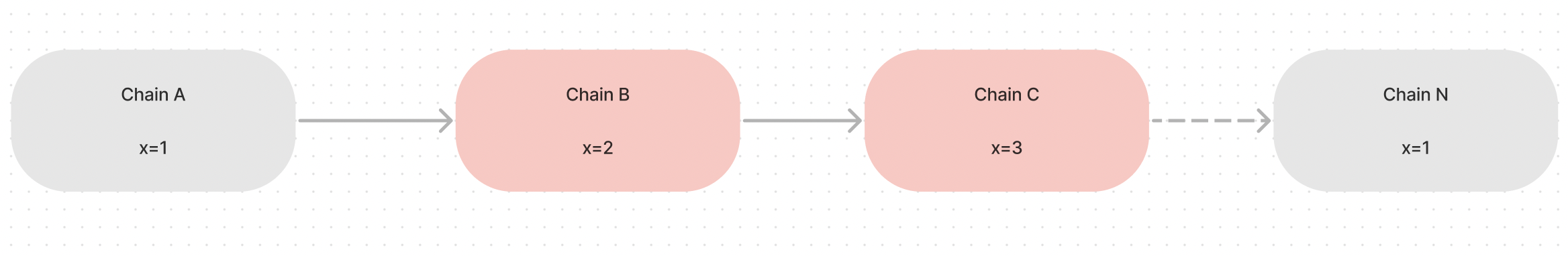 Mutable data path where intermediary chains alter the value of x.
Mutable data path where intermediary chains alter the value of x.
Way For Safer Cross-Chain Applications
There are multiple ways to exploit a cross-chain application. A few of them aren’t in the control of cross-chain application developers.
For example, a compromised validator network (or) IBC protocol can affect the application’s security.
But this article explains how an application can be designed to prevent such security threats.
-
Follow immutable data paths whenever and wherever possible: If the state change remains in the control of the application, then the possibility of tricking the application is probably null.
-
Validate state at each intermediary chain: Validating the state at each intermediary chain can prevent injecting the form into the datapath’s lifecycle.
-
Cyclic Feedback Loop: Cyclic data paths are often suggestible though the gas consumption will remain higher. The start chain would often know the end chain’s expected state change; validating it would help prevent security issues.
-
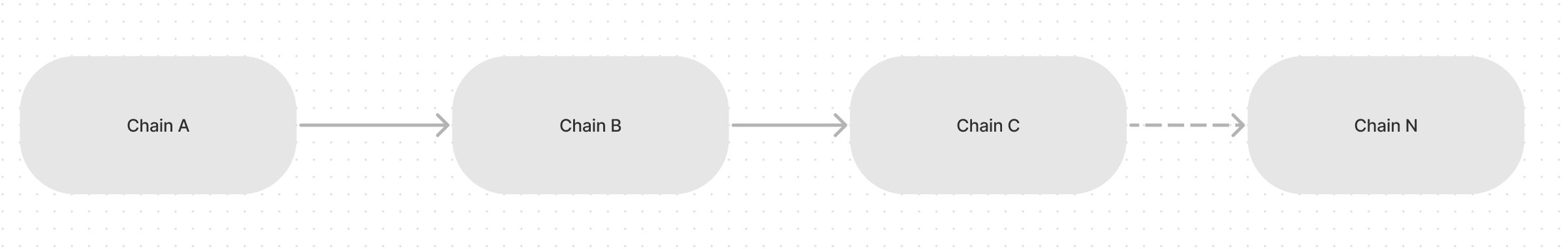
Resistive Looping: In a cycle data path, if the end chain’s state change is not desirable, execute the data path until desirable. Make sure you don’t run out of gas.
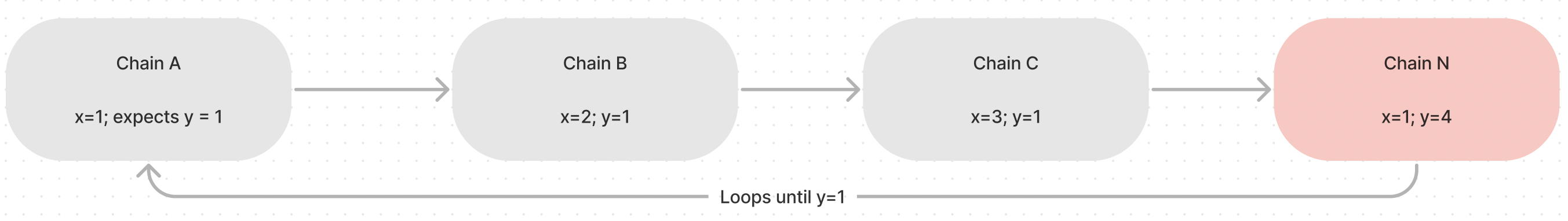 Resistive Looping
Resistive Looping
There are multiple ways to design datapaths for cross-chain applications, but this guide will help you know different ways of constructing a cross-chain data path.
Have you got queries? Feel free to contact me via somraajsujith@gmail.com or Twitter @sujithsomraaj